Video lecture: stream download
- Privacy.
- Folks generally prefer to keep personal information from parties who are unknown or untrusted.
- People disclose in order to receive something.
- Cash or discounts.
- Consideration for a loan, position, reimbursement, etc.
- Proper medical treatment.
- People expect to give information voluntarily.
- People expect the receiver to use the information only for the declared purpose.
- Transactions generate information.
- What was purchased, who purchased it, when.
- Cash is usually anonymous; not other payments.
- Both sides of the purchase have the information, but a store can collect a larger volume than an individual.
- Modern technology is hard on privacy.
- Fewer cash transactions.
- People don't expect them anymore.
- Impossible online.
- Greater ability to collect and analyze data from transactions.
- Transaction is usually recorded on a computer.
- Computer files are easily transferred, therefore data can be sold.
- Credit card numbers allow one person's transactions to be related.
- Online systems may collect data which you are not aware.
- Monitoring of activities that now move online: Web searches; social media.
- Discreet surveillance cameras and microphones.
- Fewer cash transactions.
- Sources of threat.
- Government, legitimate business, snoops or thieves.
- Information taken without consent.
- Information taken with consent, then misused.
- Information unnecessarily required by government.
- OECD Fair Information Practices.
- Limited Collection. Collection should be “limited”, legal
and not secret.
Why “limited” and not “minimal”? - Purpose. The purpose for the collected data is stated.
- Quality. The data should be relevant to the purpose, accurate, and up-to-date.
- Limitation. No use or disclosure contrary to the collection purpose, without new permission.
- Security. Holder of the data is responsible to secure against disclosure, corruption or destruction.
- Openness. The existence and purpose of the database, and contact information for the administrator should be published.
- Participation. You may discover what they have recorded about you.
- Accountability. The holder is responsible for the above.
- Limited Collection. Collection should be “limited”, legal
and not secret.
- Legalities.
- US uses several narrow federal acts, plus a few state laws.
- EU has a comprehensive law based on the OECD guidelines.
- Voluntary privacy policies: enforcement through embarrassment.
- Opt-in v. opt-out.
- The default setting on your permission to use data.
- Marketers prefer opt-out.
- Privacy mavens prefer opt-in.
- If most folks cared, it would not be an issue.
- Links. Choose your paranoia level.
- Tracking
- On-line
- Cooperating web sites share information about your purchases.
- Browsers can send a “do not track” header with your requests.
- Nothing forces the web site to honor it.
- Cell phone.
- Phone location is naturally indicated by tower location.
- Government collects a lot of this data.
- On-line
- Cookies.
- A server may ask a client to set a cookie. Has a name and a value.

- Used to keep track of login sessions, shopping carts, etc.
- User fills out account name and password, which go to the server.
- Server creates a record of the login, and returns a cookie giving the location of the record.
- All subsequent requests return the cookie. The server uses it to find the session which the client belongs to.
- Cookies are only returned to the domain which first sent them.
- Third-Party Cookies.
- Images are separated downloads, and these requests can use cookies, too.
- Images, including ads or even invisible images may send cookies
to a different domain than the page you are looking at.
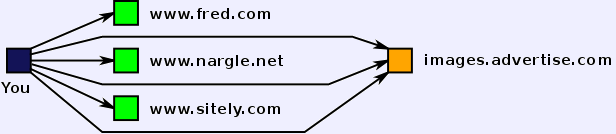
- Third party can track your activities without cooperation of the web sites you visit.
- A server may ask a client to set a cookie. Has a name and a value.
- Right to be forgotten.
- Newer notion notion advancing in Europe.
- Search engines can be legally required to remove entries about you.
- Formal charges of which you were cleared.
- It all happened 20 years ago.
- You were a minor back then.
- Some obvious sources of abuse.
- Identity theft.
- Fraudulently claim to be someone else.
- Usually due to information theft.
- Could be due to misuse or sale of legitimately-collected information.
- Computer Security
- Someone might “break in” to your computer. That means he/she manages to run any desired software on your machine.
- This can be done over the Internet.
- Risks
- Mischief. Some folks just like to be obnoxious.
- Information theft. Passwords. Account numbers. SSNs.
- Spying. Use the camera or microphone. Capture keystrokes.
- Resource theft. Use the computer to send spam or launch an attack.
- Your hacked computer is remarkably useful to the bad guys.
- How can this happen?
- Some software has a bug.
- An exploit is a carefully crafted input which causes your program to serve the hacker.
- For a web browser, an exploit might be part of a malicious web page.
- For a word processor, an exploit might be an email attachment which needs to be viewed in the word processor.
- Many exploits require the user to to something, such as visit a web site or open an email attachment.
- Some rely on what the computer will do anyway; these are usually on the server side.
- Malware: Any sort of deliberately harmful software.
- Virus: Malware inserted as part of another program that runs when it runs. Travels in downloads or email.
- Worm: Malware that actively spreads itself over the network.
- Trojan: A program which does something you want, but also something you don't. A game that that also finds passwords and sends them to the owner.
- Backdoor: A surreptitious means of access planted through some exploit.
- Rootkit: Malware that modifies your system software to cripple its ability to diagnose malware.
- Defenses.
- Keep updated (patched). Prevent the bugs.
- Use anti-virus software.
- Use a firewall (guards your network connection).
- Don't click on email links or attachments unless you know where they came from.
- Distrust pop-ups.
- Be careful where you are going, and make sure the URL is what you expect.
- Encryption.
- Used to prevent unauthorized parties from receiving your information.
- Often used for net transmission.
- Sometimes used for files.
- Terms
- cryptosystem: the combination of encryption and decryption methods.
- plaintext or cleartext: the unencrypted message.
- cyphertext: the encrypted message.
- Computer encryption is numeric.
- The message is represented in ASCII or other coding scheme.
- The characters are grouped.
- The characters in a group are appended make a number.
- The encryption and decryption works on these numbers.
- Classical cryptosystems.
- Encryption and decryption with the same key.
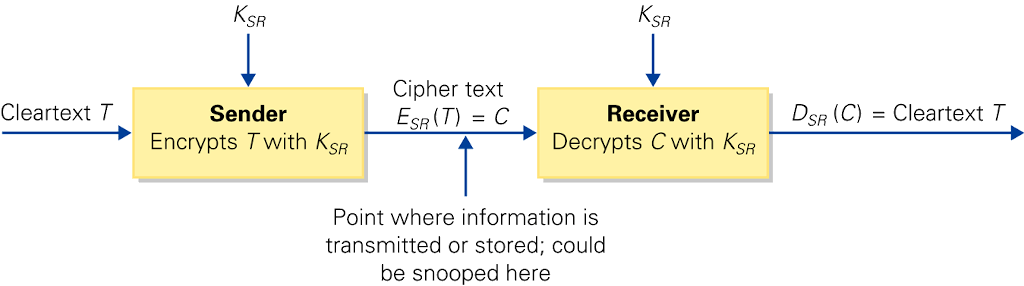
- Problem on net: how do you transmit the key?
- XOR operation used in symmetric systems.
11001001 ⊕ 01011110 = 10010111
10010111 ⊕ 01011110 = 11001001- Same bits produce zero.
- Different bits produce one.
- Property: a ⊕ b ⊕ b = a.
- How to think of it: The one bits in the key mean to invert, the zero bits mean to keep the same.
- Encryption and decryption with the same key.
- Public-Key cryptosystems.
- Encryption and decryption keys differ.
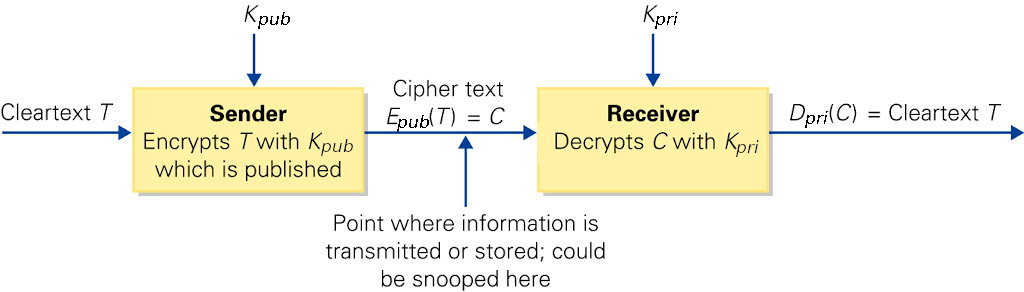
- The two keys Kpub and Kpri are produced at the same time by a single process.
- Encryption key usually published; called the public key.
- Decryption key kept secret: the private key.
- Message can only be decrypted by one who knows the private key.
- Standard technique: RSA encryption.
- Strong encryption
- Encryption and decryption keys differ.
- Backup
- Data on computers is important.
- Many terrible things can happen to that data.
- Hardware failure.
- Software errors or infection.
- Operator errors.
- Vandalism or sabotage.
- Physical accident: fire, flood, etc.
- Make backup copies which can be restored later.
- Perform the copy periodically. Businesses: daily or more often.
- Tapes, writable CDs, into the cloud.
- Best to keep copies remote from originals.