Material from Chapter 14, though the book mentions the NIC in Chapter 15.
- Methods to control access to the media so all stations don't send at once.
- Channelization Protocols.
- Divide the medium into channels. We've seen these before.
- Frequency-Division Multiple Access (FDMA).
- Time-Division Multiple Access (TDMA).
- Time-Division Multiple Access (CDMA).
- Controlled Access Protocols.
- A form of time multiplexing.
- Centrally controlled. Generally requires an extra,
low-bandwidth control channel.
- Polling.
- Central controller prompts each device to send what it has.
- Usually round-robin, though other orders or priorities can be used.
- Reservation. Similar to polling, but hosts must notify controller that they have data to send.
- These methods work well with a star topology, but can be used with others.
- Failure of the controller will disable entire network.
- Polling.
- Token Passing. A more distributed control.
- There is a special message called a “token” which represents permission to send.
- The token is passed in rotation.
- When a host receives the token, it sends any data, then forwards the token.
- Possible failures include loss or duplication of token.
- Some privileged host is allowed to create a token if it seems missing, or remove what appears to be a duplicate.
- Most often used with ring topology, also with bus.
- Wired LANs in the past optical LANs now.
- Random Access Protocols.
- These protocols use random behavior to avoid a need for centralized control.
- Coordination is local, distributed, and often after-the-fact.
- The general rule is: go ahead and try. If it fails, try again later.
- Types.
- Aloha. Historic, no longer used.
- CSMA/CD. Ethernet.
- CSMA/CA. WiFi
- Aloha Protocol
- University of Hawaii.
- State-wide radio net.
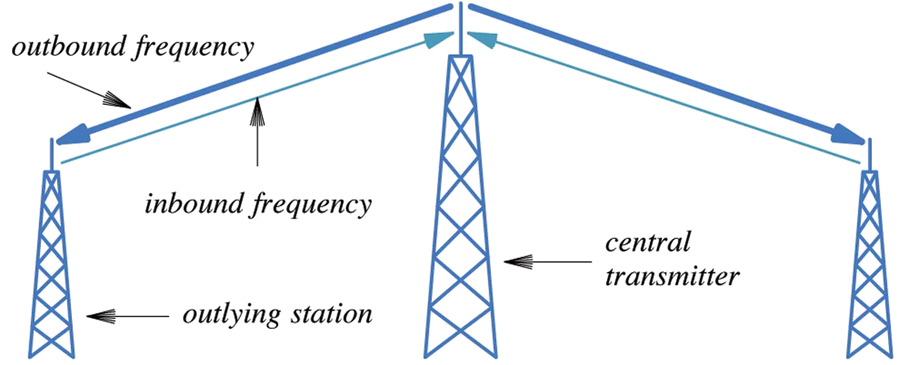
- Only the central tower sends on the outbound frequency.
- It repeats messages from outlying stations for all.
- Outlying stations send whenever they like.
- Suppose two outlying stations send at the same time.
- Combination message is garbled.
- Checksum fails.
- Message is discarded.
- Outlying sender checks for this
- Listens for repeat of the sent message.
- If not heard within a time limit, resend.
- Each waits a random amount before resend to avoid another collision.
- Carrier Sense on Multiple Access with Collision Detection (CSMA/CD).
- Ethernet.
- Wait for silence before sending a frame (Carrier sense)
- While sending, see that the signal on the bus matches what is being sent. If not, stop.
- Try again a random time later.
- For each re-send collision, double the range from which the random delay is chosen.
- Binary Exponential Back-Off
- The random delay is chosen from a range.
- On each repeated collision, the range is doubled.
- Doubling the range each time halves the probability of a new collision.
- Slows and scatters senders when the net is busy.
- Carrier Sense on Multiple Access with Collision Avoidance (CSMA/CA).
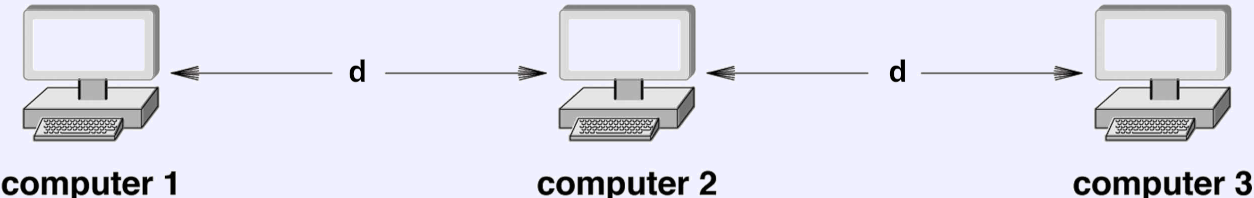
- Hidden node problem.
- Consider nodes separated by the maximum range, d, of the wireless radio.
- If Computer 1 and Computer 3 both send to Computer 2 at the same time, there will be a collision.
- But neither Computer 1 nor Computer 2 can see it because they cannot see the competing signal.
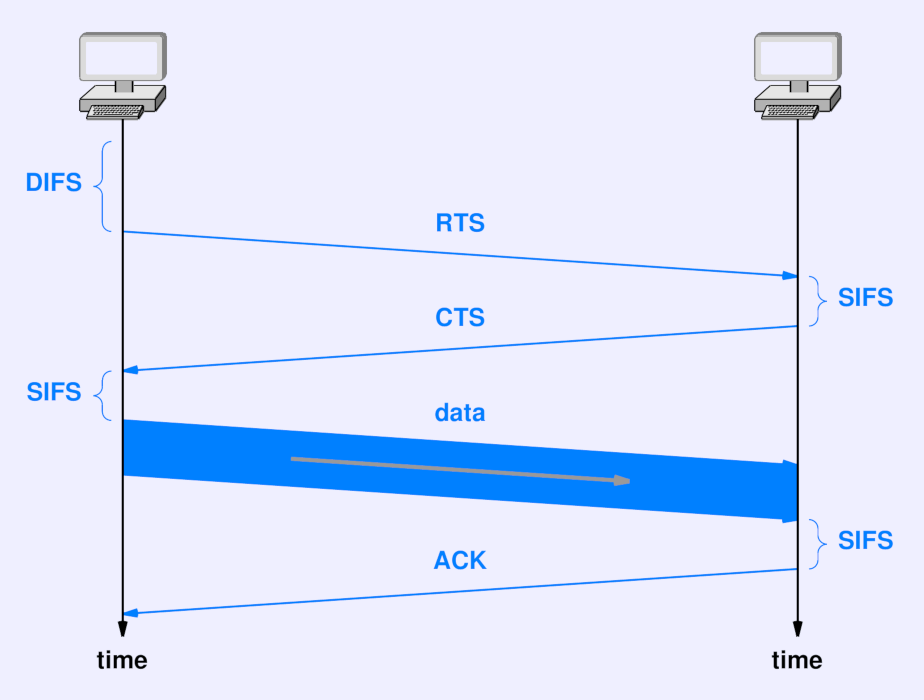
- CSMA/CA
- Send a control message to the intended recipient. Wait for a reply.
- When a reply is received, send data.
- In case of a collision, the recipient will not answer.
- Senders will then delay and re-send, as CSMA/CD.
- Collisions are detected by the recipient rather than the sender.
- Hidden node problem.
- Network Interface Card (NIC).
- Computers are connected to the network via a Network Interface
Card (NIC).
- Appears as a peripheral device.
- Originally always a separate circuit board, now usually integrated into the mainboard.
- Handles
- Frame capture from the medium.
- Runs the access protocol for sending.
- Computes and creates check bytes (usually CRC).
- Discards packets not addressed to this host.
- Contains the assigned MAC address.
- Otherwise the network would place considerable added load on the CPU.
- Computers are connected to the network via a Network Interface
Card (NIC).