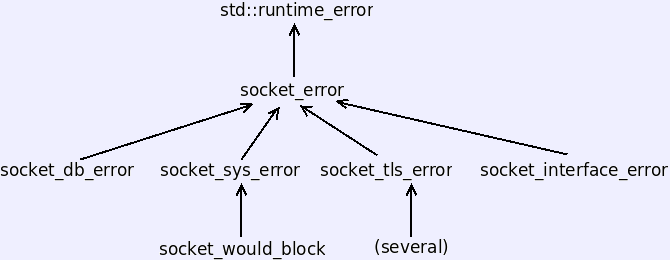
Unlike native sockets, Cleansocks throws exceptions to report errors. The library has several, all derived from the class socket_error, which is derived from the standard C++ runtime_error. Their inheritance relationships are sketched at the right, with the descendents of socket_tls_error omitted. They are listed below. The socket_error class is the base of any exception detected by this library. There are a few places which throw exceptions of exactly this type. For most purposes, if you need to catch anything, catch socket_error &.
The socket_sys_error exceptions represent errors reported from the basic socket calls. That would include creating sockets, sending, receiving, listening and accepting. The socket_would_block error wraps the system error return of the same type (hence it's a socket_sys_error). This is separated out as a convenience for programs which use non-blocking I/O and will need to handle it separately. (You're probably not doing that.) The socket_db_error is thrown by failures of host or service name performed by lookup_host or lookup_service. This division reflects one in the underlying socket interface. The socket_interface_error is thrown by misuse of the cleansocks interface. The system is designed so that most failures to follow the rules result in type errors reported at compile time, but this exception is here for when I can't figure out how to do that. The cleantlsc package throws socket_tls_error when it detects a problem. These are generally thrown as one of several descendents, which are listed below.
The std::runtime_error class and all its children have a .what() method which returns a descriptive string. The socket_sys_error and socket_db_error also implement a method .code() which returns the integer error code reported by the system. Code values will differ based on the underlying operating system, so you should avoid using .code() without some special reason.
The .what() strings for socket_sys_error and socket_db_error are the error messages provided by the underlying system, and will have different text on different OSes. Error codes for socket_db_error are error return values from the underlying socket functions, mapped to strings by the socket call gai_strerror(). For socket_sys_error, under Unix the codes come from errno and are mapped by strerror_r; on Winsock, they come from WSAGetLastError() and are interpreted by FormatMessage(), a seven-parameter monstrosity that could have come from nowhere but Redmond. For socket_tls_error, some exceptions follow from error reported by OpenSSL, and contain the OpenSSL's error message. Errors detected by logic in the cleantlsc wrapper code provide (supposedly) appropriate messages.