This page covers material from Ch. 12 in the text. Even swiped the title.
- Introduction. The problem of keeping your marbles.
- A PHP script runs, produces an output page and exits.
- Variable values are lost when the script exits.
- When pages are related, it is necessary to retain information
between these executions.
- Executions can pass values to themselves through hidden form fields (Ch. 11).
- Cookies (this chapter) are another way for a script to have the web browser pass information to a later invocation. Cookies can be longer-lived, and passed to invocations other than the very next.
- Executions can retain data in the server file system using a database or plain files on the server.
- PHP provides sessions (this chapter) which allow PHP scripts to store information in the server where it can survive from one script to another.
- Use of the server-side methods usually requires use of a browser-side
as well to identify which information is relevant.
- A hidden form field might contain an identifier to locate the database record for a shopping cart.
- Sessions typically use a cookie to store an identifier indicating which session to use.
- Frequently, web pages allocate resources (think: spend money, but there are many other possibilities). In that case, we want to know if the user really is who he/she claims.
- This is the authentication problem.
- Usually, the user sends an account an password.
- More sophisticated methods are beyond this course.
- Once authenticated, multiple pages will obey the allocation request.
- The authorization status must be passed from page to page.
- And must not be easily forged.
- Cookies
- Cookies were invented by the former Netscape Communications Corp. as a better solution for data retention.
- Technology
- Each HTTP message contains headers, which provide control info.
- Cookies use SetCookie and Cookie Headers.
- The server asks the browser to remember a key/value pair when it sends a result.
- On the next request (only to the same server), it sends that info back.
- The server may assign an expiry date to the cookie, otherwise it is deleted when the browser is closed.
- The browser is not obligated to honor the Set-Cookie header, but most do.
- Using Cookies in PHP.
- setcookie specifies a cookie to be sent
with the page generated.
- Only the name parameter is required.
- Must be called before any non-PHP sections, and before any echo.
- Set the expire for the cookie to last longer than the browser session. time() + 3600 lasts an hour. (Time is a Unix() time, seconds past the start of 1970, GMT.)
- The path and domain restrict where the cookie will be returned to. The domain can only be restricted within your own; one site cannot set a cookie for another.
- Cookies sent requesting a page appear in $_COOKIE['name'].
Use isset($_COOKIE['name']) to see if it was sent.
[ Cookie Example Source ]
- setcookie specifies a cookie to be sent
with the page generated.
- Authentication
- For our purposes, accepting and checking some kind of ID and password.
- HTTP Authentication.
- The HTTP protocol contains a password system using headers.
- The server requires login credentials from the browser, and the browser requests them from the user.
- The credentials are entered via a dialog generated by the browser, not through an HTML form.
- We'll not be using it.
- Using a form
- Usual way these days is to accept creds using a form.
- Input tag type password is like text, but shows stars when you type.
- Check the username/password pair against a database.
- Saving a password.
- Passwords must be stored on the server.
- Obvious target for hackers.
- Usually, the password is not saved, but instead a crypto hash is
used.
- A cryptographic hash function is a one-way function, meaning it is very difficult to invert.
- If you know the correct hash, you can test a password by hashing it and comparing the results.
- But you cannot (in a reasonable amount of time) find the password
from the hash.
[ Some Hash Examples. Source ]
- Best practice is to use a slow hashing algorithm, with salt.
- Salt is some extra string added before hashing, so the same password will have different hashes.
- Text author does it himself, but easiest is to use password_hash. (This function may be newer than the text.)
- Sessions
- PHP allows scripts to create sessions, where they may store data on the server.
- By default, a cookie is generated which identifies the session.
- Use session_start to start using a session. Do this before generating output.
- Values are kept in $_SESSION['value'].
- When a user authenticates, this is often recorded in a session.
- Guessing Game With Sessions.
- [ Guessing Game Source ]
- Doesn't put the guess in the page source with a hidden field.
- Resumes even across window closing.
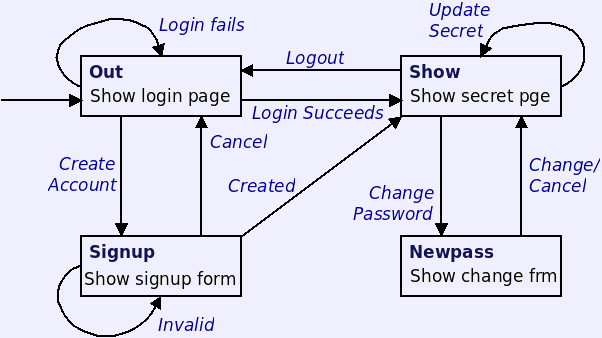
- [ Secret Example Source ]
- Allows you to keep some secret text protected by a password.
- Demonstrates creation and use of passwords stored safely on the server.
- A single PHP script generates one of four pages based on the state of the session.
- The state is stored in the session, and changes when the user submits a form.