- Any data communication system is susceptible to errors.
- Major error sources
- Interference: Unwanted energy enters the system from outside.
- Distortion: The shape of the signal is not fully preserved by the system.
- Some frequencies may be blocked while others transmitted.
- Optical fibers cause waves to disperse.
- Attenuation. Energy is lost as the signal travels over distance.
- How errors present themselves.
- Single-bit error: An isolated bit is inverted.
Often due to short interference events.
- Burst errors: Multiple contiguous bits are inverted
Often due to longer-term interference.
- Erasure/ambiguity: a portion of the signal is no longer identifiable
as one or zero.
- Approaches.
- Automatic Repeat Request (ARQ): The receiver detects the error
and requests a resend.
- Forward Error Correction (FEC): The receiver detects and fixes
the error.
- Collectively, channel coding.
- Key Idea: Redundant information.
- Detection and correction involve sending extra (redundant)
information along with the message contents itself.
- The redundant information is computed from the message by the
sender, and verified by the receiver.
- Simplest form.
- For detection (ARQ): Send two copies of everything. If they agree, assume
the transmission is correct. Otherwise, request re-transmission.
- For correction (FEC): Send three copies of everything.
- If all agree, no error.
- If two out of three agree, assume that version is correct.
- If all three differ, either fail for fall back to ARQ.
- Practical systems use less redundant information than that simplest
form.
- Limitations.
- Systems assume that transmission works correctly most of the time.
- Failure to detect, or faulty correction are always possible,
but should be very unlikely.
- Code types
- Block Error Code: Information is divided into blocks. Redundant
info is attached to each block, and is a function of it.
- If k bits of payload data require r bits of redundancy,
the system is an (n,k) encoding scheme, where n=k+r.
- A measure of the scheme's overhead is the code rate:
- Convolutional: Message is treated as a bit stream, and the
redundant information at any point is a function of all before.
No fixed-size blocks.
- Single-bit parity: Simple block error detecting code.
- Operation.
- Typically, a block is one byte. Each block is extended by one
redundant bit.
- For even parity: The number of ones in the nine-bit group should be
even; for odd parity, odd.
- Sender computes the correct bit, receiver verifies it. Incorrect
parity indicates a bit error.
| Original Data | With Even Parity | With Odd Parity |
| 00000000 | 000000000 | 000000001 |
| 10001110 | 100011100 | 100011101 |
| 00100011 | 001000111 | 001000110 |
| 11111111 | 111111110 | 111111111 |
| 01100010 | 011000101 | 011000100 |
- This is a (9,8) coding scheme.
- How well can it work?
- Obviously, will only catch errors where the number of incorrect
bits is odd.
- Assume that the probability of a bit error, p is small.
- Assume that bit errors are independent (that is, no burst
errors).
- Then
- The probability of an error in exactly one bit (detected) is
p(1−p)8.
- The probability of an error in exactly two bits (undetected) is
p2(1−p)7.
- If the assumptions are true, the most-likely detected error is
much more likely than the most-likely undetected error.
In fact, any error beyond one bit is very unlikely.
- The assumptions need not be true.
- The Hamming distance between two bit strings is the number of
bits which must change to get from one to the other.
| d(1010,0100)=3 | d(0001,0000)=1 | d(1001,0110)=4 |
| d(1100,1110)=1 | d(1101,1010)=3 | d(0011,0110)=2 |
- Codebook
- For an (n,k) coding scheme, there are 2n possible
messages, of which 2k are valid.
- The set of valid ones is called the codebook.
- A change to an entry in the codebook may produce another codebook
entry, or an invalid bit pattern.
- Ideally, any change to a codebook entry would produce an invalid one.
Obviously, this is impossible.
- For single-bit parity on a byte, change any one bit produces an invalid,
two bits produce another codebook entry.
- The minimum Hamming distance between any two code entries is denoted
dmin. Measure of the scheme's strength.
- For parity, dmin=2.
- Errors of more than
dmin−1 bits may go undetected.
- Row And Column (RAC) parity: Block error correcting.
- Arrange the data as a two-dimensional array.
- Compute a parity bit for each row and each column. (And another
for the whole thing.)
- The example at right is a (20,12) scheme which arranges the
payload arbitrarily in a 3x4 grid.
- The position of a single-bit error can be
determined by which row and column shows a parity error.
- The error can be corrected by simply inverting the indicated bit.
- RAC can correct single-bit errors, and detect (but not correct) any
error involving a larger odd number of bits.
- It can also detect errors with small even numbers
of bits.
- Hamming codes: Block error-correcting.
- Number bit positions in the transmission starting at 1
(instead of zero for once).
- Each position indexed by a power of two is a parity bit; other positions
are payload data.
- Each parity bit is computed over some of the data bits based on
the position values expressed in binary:
- Positions which are powers of two contain
parity bits.
- Other positions contain data bits. A data bit contributes to each
parity bit corresponding to the place value of a one in its
position number.
- For instance
- The bit in position 13 is included in the
parity bits at 8, 4 and 1.
- The parity bit in position 1 is computed over all the data
bits in odd positions, since they have ones in their ones place.
- The parity bit in position four is computed over data
positions, 5–7, 12–15, 20–23, etc.,
up to the maximum number of data positions.
These are the locations which have ones in their fours place.
- Since data bits are not powers of two, every one is
covered by at least two parity bits.
- Every parity bit covers a different set of data bits.
- For a single-bit error, the receiver simply totals the
positions of mismatching parity bits to find the position of
of the error bit.
- A (20,15) example.
- Here is a correct transmission. The parity positions are indicated.
If you hover over a parity bit, the figure shows which data bits
it covers. If you hover over a data bit, the figure shows which parity
bits cover it.
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 1 |
- Suppose one of the data bits is transmitted incorrectly. The
receiver would see something like this:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 1 | 0 | 1 | 1 | 0 | 1 | 1 | 1 | 1 | 0 | 1 |
The parity bits that cover data bit 10 are 2 and 8, so they detect that error,
and together identify the incorrect bit.
- Here's another:
| 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10 | 11 | 12 | 13 | 14 | 15 | 16 | 17 | 18 | 19 | 20 |
| 0 | 1 | 1 | 0 | 0 | 1 | 1 | 0 | 1 | 0 | 0 | 1 | 0 | 0 | 1 | 1 | 1 | 1 | 0 | 1 |
- If the error is a parity bit, it will be the only parity bit showing
the error, and will denote itself.
- Internet Checksum: Error detecting.
- A checksum is a value computed over the message contents. It is
appended to the transmission by the sender, and checked by the receiver.
- The Internet checksum is a 16-bit number computed over the contents
of an Internet datagram:
- Break the message into 16-bit units; pad at the end with zeros
if needed.
- Add the 16-bit units. Any carry-out past the 16-bit size is
added in as well.
- Invert the sum.
- If the result is zero, substitute all ones (65535 decimal).
- Use
- The sender computes the checksum, and places it in the header.
- The receiver verifies it by
computing the checksum over both the message and the
checksum sent. Zero indicates a correct result.
- The sender may send a checksum value of zero to disable the
checksum mechanism. The receiver assumes the message is correct.
- Example.
- Cyclic Redundancy Codes: Error detecting.
- Like a checksum, a function of the data appended by the sender and
checked by the receiver.
- Used in high-speed networks, such as Ethernet.
- Properties
- Can operate on variable-length data (as a checksum can).
- Excellent error detection ability.
- Fast hardware implementation.
- The computation can be represented in several ways.
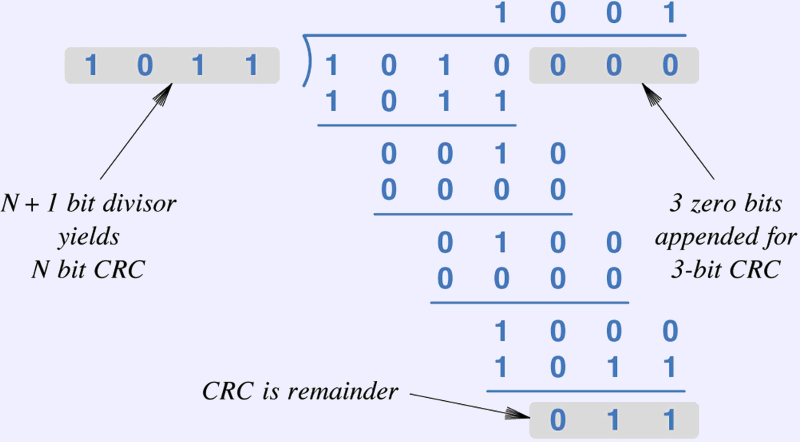
- The remainder of an odd sort of binary division, where subtraction is
replaced by xor (no borrowing).
- The divisor can be “subtracted” when the result has a zero
in the high bit.
- Divide the message by a some chosen constant.
- The division of one polynomial by another.
- The coefficients are the bits, so all are 1 or 0.
- The example at right (1011 into 1010000)
is x3+x+1 divided into
x6+x4.
- The divisor is called the generator polynomial
- Better generators are those divisible only by themselves and 1.
- Generator with more than one non-zero coefficient can detect all
single-bit errors.
- High-speed hardware mechanism.
- Hardware for the 1011 divisor
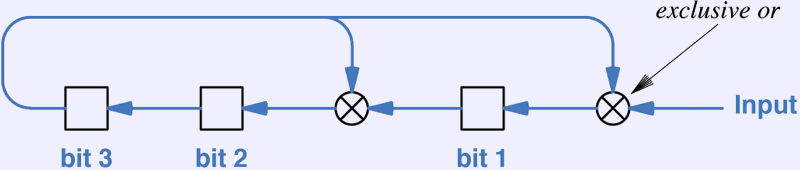
- Shift the message in one bit at a time.
- Follow the message with zeros the length of the CRC to compute
a new CRC.
- Follow the message with a received CRC to test it. Will produce
zero if correct.
- Shifting and XOR are cheap and fast.
- Methods, again.
- FEC can use methods such as RAC or Hamming codes that allow for
correction.
- ARQ can use either, but using a correcting code for just ARQ is wasteful.
Probably use a detecting scheme like checksum or CRC (or possibly
simple parity).
- An FEC system can also use ARQ as a backup when there are too many
errors to correct.