- Networking is growing quickly.
- The Internet was a research product in 1980; now its an essential.
- Huge industry to provide networking and related services.
- Complexity
- No single underlying theory for the whole field.
- Inconsistent terminology.
- Different sub-fields tend to invent their own names for the same things.
- Marketing v. engineering.
- Five Key Aspects
- Network Applications and Programming.
- Writing code which uses the network.
- Does not require deep understanding of the net technology, just
the API to use it.
- Data Communications.
- The physics of getting a signal from one computer to another.
- Making those physical phenomena deliver bits.
- Packet Switching and Networking Technology.
- Telephone and telegraph establish a dedicated path
between each pair of endpoints.
- Modern computer networks move packets through a network of shared
connections. This is a big change.
- Uses resources more efficiently, but a packet is not guaranteed to
to have a way through, producing loss and delay.
- Internetworking and TCP/IP.
- A single standard to connect various, and very different, types
of network together.
- An abstract networking interface implemented in terms of various
types of (packet-switched) hardware networks.
- Etcetera. Performance, security, remote automation.
- Public and Private.
- Public networks are available to the public, such as those run by
any ISP.
- Private networks belong to an organization and serve its members.
- Your home network.
- Office networks.
- The campus network.
- Classifications
- Consumer.
- Small/Home office (SOHO).
- Small to Medium Business (SMB).
- (Large) Enterprise.
- Access, not ownership.
- Comcast runs a public network which is privately owned (by Comcast).
- The office network in any government agency is a publicly-owned
private network.
- Protocols and Standards.
- For computers to communicate, they must agree on a thousand things:
voltages, timings, message formats, data representation,
addressing, error handling, etc.
- These are specified by a networking protocol (or
communications protocol.
- Protocols are organized into protocol stacks (or families).
- A stack is arranged in layers.
- The notion is similar to that of federal government: the separate layers
each deal with separate issues.
- Communicating computers must conform with each set of rules.
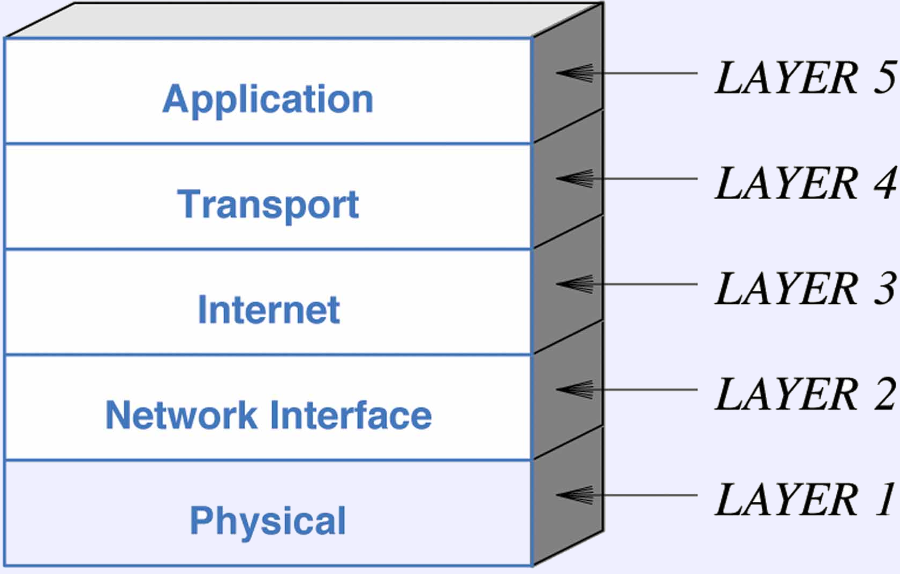
- The TCP/IP Stack
- Physical Voltages and other electrical properties, radio frequencies,
etc.
- Network Interface (MAC): Hardware device addressing, protocols to
share the physical medium, packet sizes and format.
- Internet: Internet addressing, packet structure, routing and error
reporting.
- Transport: Provide for communication between endpoints.
Maximum data rates, congestion avoidance, reliable delivery.
- Application: Rules to perform a particular service, e.g.,
HTTP, email protocols, multimedia delivery protocols, etc.
- Note: Addresses used at the network layer (MAC addresses) differ
from those used at the Internet layer (IP addresses). MAC
address format depends on the type of hardware in the network, and
IP addresses does not.
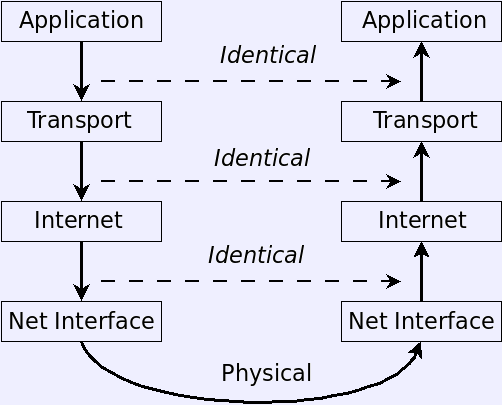
- Messages in the stack.
- Messages travel down from the application, through each layer of the
stack, across the wire, then back up through the stack to the
application on the other side.
- Each layer thinks of itself as communicating with the same layer
on its peer.
- Each layer may add a header to the message (or make other changes)
as the message goes down. These are removed by the receiver as the
message goes up.
- The headers allow each layer to communicate with its peer.

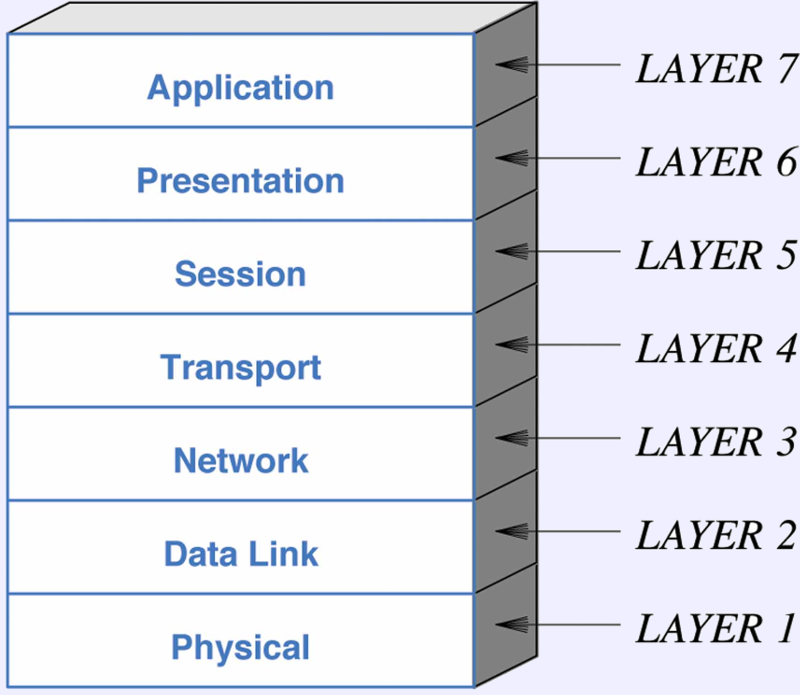
- The OSI model.
- From the International Standards Organization (OSI from ISO).
- Intended as a general model; does not refer to any specific
implementation or family.
- Engineers often refer to these layers.
- Older than the TCP/IP stack
- Does not have an internet layer, so we let the
network layer be that.
- TCP/IP essentially combines ISOs Application, Presentation and
Session layers into its Application layer.