- Where do routing tables come from?
- Static routing: Established by the administrator, and is not changed
by information from the network itself.
- Table may just be stored in a configuration file loaded at boot time.
(Rare these days.)
- Table may be built with info from DHCP.
- Or some combination of these two.
- Network-related services may modify the table when they come up or
down, but this would still be considered static routing.
- Bringing a network interface up or down.
- Starting or stopping a VPN service.
- Typical case: User machine with just a local net and default router.
| Net | Mask | Next |
|---|
| 128.10.0.0 | 255.255.0.0 | direct |
| 0.0.0.0 | 0.0.0.0 | 128.10.0.100 |
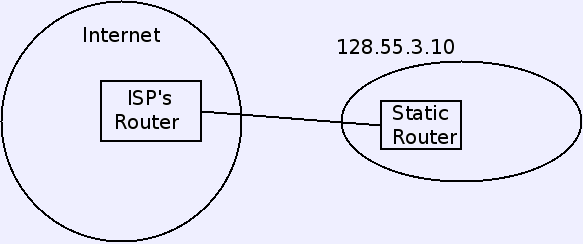
- Routers connecting a small organization to its ISP may also be able to
use static.
- Dynamic routing: Routing information propagates, and
tables are updated as the network changes.
- Routers in the middle of large organizations, or in
the middle of the public Internet,
need dynamic routing.
- Autonomous Systems.
- A group of routers under the same administrative authority.
In practice, a fairly large organization.
- A large corporation, ISP, or university.
Google, Microsoft, Comcast, MIT
- Smaller organizations operate as part of their ISP's AS.
Mississippi College, your house
- Very large companies, usually ISPs or other networking organizations,
may divide themselves into multiple ASs.
- AS's have numbers.
- Routing information is spread in a two-level hierarchy.
- Within an AS, routing information is spread using
an Interior Gateway Protocol (IGP).
- Each AS may choose its IGP, or possibly use static routing.
- Packets are routed between routers inside the AS.
- The protocol tries to pick a good route among the possible ones.
- Between AS's, routing information is spread using an
Exterior Gateway Protocol (EGP).
- All AS's use the same EGP,
Border Gateway Protocol (BGP).
- Packets are routed between AS's.
- Each AS exports only limited information about itself
to the EGP.
- The protocol attempts to find some route, since it doesn't
know enough about AS internals to compare.
- Routing Information Protocol (RIP)
- An IGP.
- Distance vector routing.
- Each router maintains a routing table with costs in hops.
- It periodically sends this information to its neighbors.
- Updates are sent as UDP packets.
- In v. 1, updates are broadcast.
- In v. 2, multicast is allowed so so only routers need to bother.
- A host may use a listen-only version.
- Extended version for IP6 addresses.
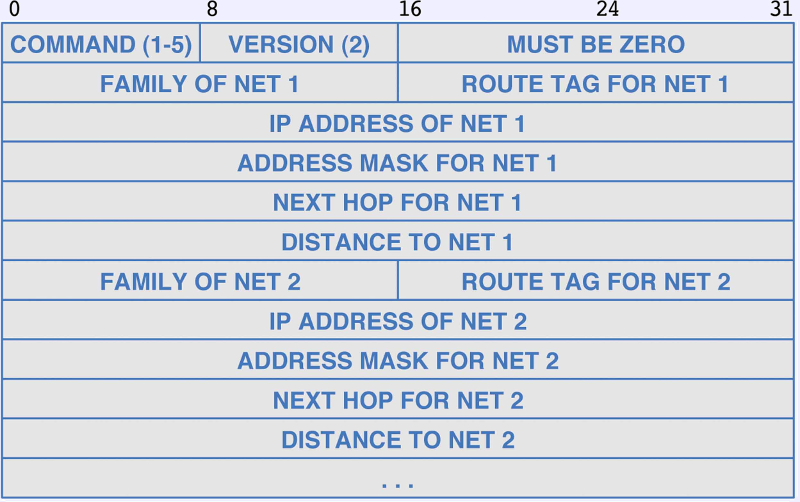
- Packet format
- The address family specifies the type of address, pretty much always
IP4 (code 2). May also have a special code for extensions.
- The tag field distinguishes routes advertised by RIP from
routes imported from another IGP or from an EGP.
- The packet is basically a copy of the routers routing table.
- RFC 2453.
- Security.
- Original version(s) were easily hackable by spoofing.
- Later versons allow routers to send password hashes to authenticate.
- Routers configured to know each others passwords; can ignore spoofed
RIP messages.
- RFC 2082 and RFC 4822.
- Open Shortest Path First Protocol (OSPF)
- An IGP.
- Message are encapsulated directly in hardware packets.
- All messages are authenticated.
- Routes may be imported from an EGP or other external source.
- Uses broadcast to find neighbors (Hello protocol), but not to
send routing data.
- Uses link-state rather than distance-vector.
- Each router is configured with a graph of the network, with
link costs set administratively.
- Routers find the state of their interfaces and adjacent routers,
and share with other routers.
- Each router can compute the shortest path to a destination locally
using its graph plus the received state information.
- Network may be organized into a hierarchy.
- The network is divided into blocks of adjacent routers, called areas.
- Routers in an area send status updates to each other router in
its area.
- Routers on the edges of areas, with connections to each,
maintain state information for each area separately. These are called
Area Border Routers, since they can move packets into or out
of an area.
- The ABRs and other non-area routers form the backbone, which is
treated as a special area.
- Routes within an area are computed by its routers.
- Packets between areas are routed to the backbone, through the
backbone, then within the destination area.
- Areas reduce traffic, since routers in different areas don't need
to update each other.
- RFC 2328 and
Cisco
wiki entry..
- IS-IS
- A protocol similar to OSPF, originally proprietary to Digital Equipment
Corporation (DEC).
- Grew up together and
shared
many ideas.
- Eventually, DEC dissolved, and an IP version was defined.
- Largely unused for a long time while OSPF was used broadly,
thereby accumulating crud.
Now experiencing new interest because it is simpler and scales better.
- BGP
- Describes routes between ASs. Routes are from, to and through
ASs, not routers.
- The administrators of an AS decide which routers
- will accept traffic from outside to a destination inside,
- will send traffic out of the AS,
- will accept outside traffic going through the AS and out another way.
- An AS is thereby classified as transit
(will route traffic through) or stub (can or will not).
- These routers run the BGP. They communicate with other such routers
in adjacent AS's.
- Communications is over TCP connections.
- A BGP reports to its neighbors
- Routes to or through its own AS that it is configured to report.
- Routes to other destinations that it builds with info from other
routers.
- These routes link ASs; no AS internal information is transmitted.
- BGP uses some rules to choose relatively better routes, but it
does not have enough information to determine
an optimal route.
- Multicast.
- IP has always allowed for multicast.
- Not widely used in the internet as a whole.
- Sometimes used within an organization.
- Routing is difficult.
- Have to find all the recipients, which could be anywhere.
- Nodes which are not recipients can still send to one.
- Nodes can come and go at any time.
- Internet Group Message Protocol (IGMP) defines messages
to control group membership.
- A host sends an IGMP message to a standard multicast address to
join or leave a group.
- No established standard to determine routing. Three main approaches
- Flood-and-prune
- Used on LANs.
- When a multicast packet arrives, send it to all other destinations.
To avoid cycles, packets are only forwarded away from the source
node, according to the regular unicast routing table.
- If a router finds that no recipient actually wants the packets,
it informs the upstream.
- The upstream will quit forwarding. If all its downstream don't
want the packet either, it will notify its sender. Thus the
tree is pruned.
- Configuration-and-tunneling
- Used to connect remote LANs.
- A router on each LAN is configured to know about the others.
- Uses hardware multicast locally, and tunnels for the router
to each other site with needs it.
- Core-Based Discovery.
- Can be used for larger scale.
- Designate a core unicast router.
- Send a membership request to the core. Each router that passes it
adds a multicast routing entry back to the sender.
- When reaching a router that is already participating, the sender is
connected.
- When a non-participant sends to the multicast address, send to the
core. When it first reaches a participating router, it is
multicast from there.
- Protocols
- Distance Vector Multicast Routing Protocol (DVMRP).
- Used by former MBONE.
- Broadcasts locally, uses distance-vector to find routes between
participating localities.
- Core Based Trees (CBT). Application of Core-based discovery.
- Protocol Independent Multicast — Sparse Mode (PIM-SM).
Variation on CBT.
- Protocol Independent Multicast — Dense Mode (PIM-DM).
- For local areas.
- An application of flood-and-prune.
- Multicast Extensions to the Open Shortest Path First Protocol (MOSPF).
Uses link-state like OSPF, so the multicast graph is essentially
constructed by the administrator.