Some quick notes on three useful security-related topics.
- Firewalls.
- A firewall is a router, with two modifications:
- It may examine parts of the packet in addition to the destination, and use them to match packets under relevant rules.
- It has the additional destination, discard. (A.K.A., the floor, the bit bucket or /dev/null.)
- A firewall is generally used as the router which forwards packets in an out of some organization.
- It has a routing table and performs the routing function in the usual
way, with additional rules configured by the admin. Such as:
- “Block all inbound traffic using port 23.”
- “Discard packets arriving on the external connection whose source address is in the range of internal addresses.” This would be a remote machine pretending to be local. Can't be good.
- “Discard packets arriving on the external connection which have the SYN bit set.” This packet is attempting to connect to a service. If you don't have any externally-visible servers, this packet has no business here.
- If you know that 72.65.67.75 is run by evil people (or maybe just your business competitor), you might block any outbound traffic which is going there.
- Main classes of firewalls.
- Stateless firewalls examine each packet in isolation.
- Stateful firewalls retain history to relate one packet to another.
- They primarily track connections.
- For instance, a stateful firewall can have a rule like: “Block all incoming traffic from port 80 unless bound to a a local machine that sent a request outbound on to port 80 on that same machine within the last 10 minutes.” This would let you broadly block traffic, but allow responses to HTTP requests.
- Stateful firewalls can become impractical if the traffic volume is very large.
- Content filters examine the actual payload. These must understand an application protocol (usually HTTP) and are limited to filtering such traffic.
- A firewall is a router, with two modifications:
- NAT Routing.
- Network Address Translation is a technique developed to stretch the supply of IP4 addresses.
- Certain IP address ranges are designated private.
- Ranges are: 10.0.0.0/8, 172.16.0.0/12, 192.168.0.0/16
- These are not assigned and may be used by anyone.
- Routers on the larger Internet drop packets destined to private addresses.
- Organizations use private addresses internally, and place NAT routers
at the edge to translate.
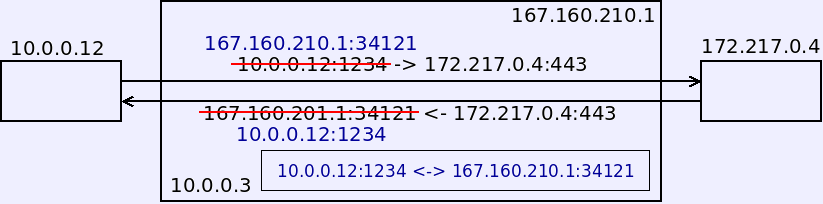
- A NAT router has one interface using an internal private address and another with an external public address assigned to the organization.
- When an internal machine sends a packet out, the NAT router substitutes the packet source with the public IP and a port of its own choosing.
- The NAT router records this choice.
- When the external host answers, it responds to the public address which is attached to the NAT router. NAT makes the reverse substitution from the stored translation.
- The NAT router assigns different port numbers to different conversations so it can support several conversations on several internal hosts at once.
- Inbound packets are all directed to the same IP address, but to different ports. The NAT router uses the destination port number to choose the right translation.
- Translation records.
- When an outbound packet creates a translation record in the NAT, that record is generally retained until it is unused for a while.
- An inbound packet will be dropped if there is no pre-existing translation record for it.
- A TCP connection through the NAT will generally fail if the NAT drops its translation record. Many TCP implementations send redundant “keep-alive” acks during quiet periods to freshen the NAT record.
- If it is desired that some internal host be accessible from outside, a translation may be stored permanently for it.
- This all means a NAT has some firewalling side-effects, but all of them could be accomplished with a plain firewall absent a NAT.
- A NAT is logically different from a firewall, but they are almost always
implemented together.
- They go in the same place in the network.
- A NAT and a stateful firewall require nearly the same record-keeping, so why duplicate effort?
- NAT allows an organization to connect many hosts to the Internet using only one or a few public addresses.
- Tunneling and VPNs.
- Encapsulation need not always walk up the protocol stack.
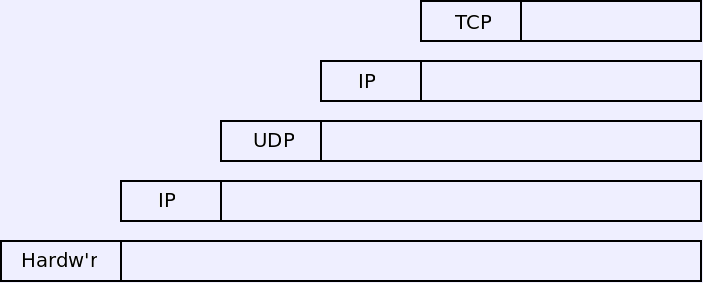
- TCP segments can be sent as UDP messages. That allows TCP to be
carried as UDP traffic. (The IP layer must be included again if you
want to deliver the TCP to a destination different from the UDP.)
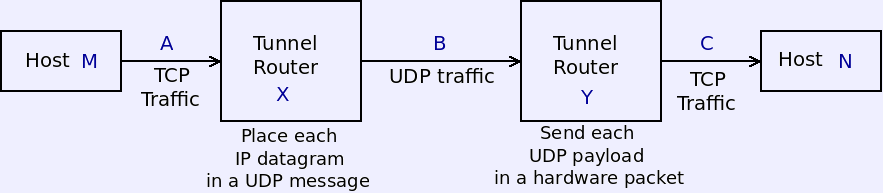
- In segment B, routers and firewalls see UDP traffic destined to router Y, rather than the true destination.
- In this example, the UDP segments contain IP, it could be any protocol, at any level of the stack, including hardware segments.
- VPN
- Tunnel router X encrypts each IP datagram before placing it in a UDP message. Router Y decrypts it.
- Segment A and C might be LANs belonging to the same organization in different locations.
- Segment B can safely cross the public net without revealing private info.
- A tunnel router may be a physical router, or just a software program running on host M and/or N.
- In a common arrangement, X is software on the laptop of a traveling or remote employee who may use it to safely connect to the organizational LAN.
- Penetrating firewalls.
- If segment B contains a firewall, it will not see the true destination
and other properties of the tunneled traffic.
- For a VPN, that information should be quite hidden from the firewall.
- Even if not encrypted, the firewall probably won't know to check.
- VPNs can therefore
be used to bypass blockages created by firewalls. The firewall does
not see the information it needs to apply its rules relative to the
final destination of the traffic.
For all the usual purposes.
- Violate terms of service for the local network.
- Information theft.
- Corporate or political espionage.
- Bypass government information controls.
- Firewall administrators
- Will often attempt to block known tunneling hosts.
- But it's pretty easy to just set up a new one.
- If the administrators control the internal network also, they may attempt to prevent installation of VPN software there.
- NATs often treat TCP and UDP differently, so a tunnel can sometimes be used to change the way a NAT treats your traffic, for good or ill.
- If segment B contains a firewall, it will not see the true destination
and other properties of the tunneled traffic.
- Note: I have sometimes heard the administrative unblocking of a port in a firewall described as “opening a tunnel.” Thats not how I'm using the term here.
- Encapsulation need not always walk up the protocol stack.